The alarming lapse in data security protocols demands urgent attention and decisive action. Failure to address this issue effectively not only puts individuals at risk but also undermines the trust in governance
In today’s digital age, where information is power, safeguarding sensitive data is paramount. However, recent revelations have shed light on a concerning trend – an alarming lapse in data security protocols, particularly within government institutions. The breach of trust and the potential ramifications for individuals and society at large underscore the urgent need for robust measures to address this critical issue.
You can also read: Bangladesh’s Banking Sector Faces Tk 5.50 Trillion Non-Performing Loans Surge
The National Telecommunication Monitoring Centre (NTMC) discovered that this private information was being sold through 21 WhatsApp, 48 Telegram, and 720 Facebook groups and pages, which collectively have 32 lakh (3.2 million) members and followers.
Between March 25 and April 25, the login IDs of the two police officers collected significantly more data than any other users.

Breach of Trust: Exploitation by Government Employees
The NTMC’s server serves as a repository for a treasure trove of personal data, including NID cards, passports, driving licenses, and call detail records. Nearly 500 officials from 42 organizations have access to the National Intelligent Platform (NIP), where they can log in and access this data for verification and investigation purposes. However, recent breaches have exposed glaring weaknesses in the data security infrastructure and underscore the urgent need for enhanced security measures.
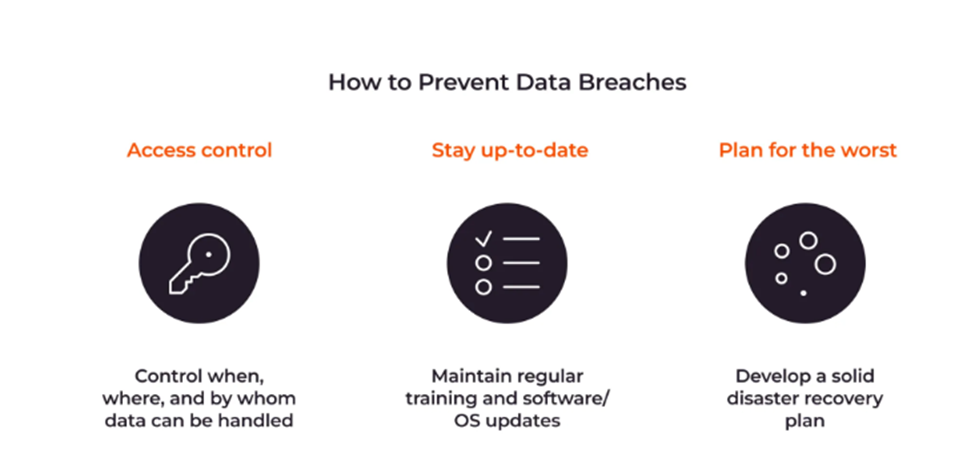
How to Prevent Data Breaches
While prevention is ideal, even the most secure systems can be vulnerable to human error and breaches. Here’s a quick response guide to minimize damage if a breach occurs:
Detect: Implement robust detection systems to monitor for signs of illicit access or suspicious activities. Utilize tools like Gcore WAAP for real-time scanning of incoming traffic, ensuring swift detection of potential breach attempts.
Contain: Prioritize containment once a breach is detected to prevent further damage. Gcore WAAP can automatically block and isolate data identified as part of attacks, minimizing the risk of unauthorized access and thwarting malicious traffic.
Eradicate: After containing the breach, eliminate underlying security weaknesses by removing malware, closing unauthorized access points, and patching vulnerabilities.
Report and Recover: Communicate the breach to affected parties and develop a recovery plan, including data restoration and policy updates. Collaborate with security experts to develop a protection plan to prevent future breaches.

Widespread Impact: Threat to Security and Privacy
The extent of the breach remains unclear, but the dissemination of personal data through social media platforms paints a grim picture. Personal data, including NID details, being sold through WhatsApp, Telegram, and Facebook groups and pages with millions of members and followers, poses a severe risk to privacy. Such data can be exploited for nefarious activities, ranging from identity theft and financial fraud to espionage and cyberattacks. The potential consequences for individuals are dire, with victims bearing the brunt of the fallout for years to come.
Call to Action: Addressing the Root Cause
The NTMC’s revelation should serve as a wake-up call for the government. Relying on existing data security protocols is insufficient to address the evolving threat landscape. What is needed is a comprehensive overhaul of the data security infrastructure, coupled with stringent security and accountability measures for officials and organizations with access to sensitive data. The NTMC’s recommendations must be carefully evaluated and swiftly implemented to restore trust and safeguard citizens’ privacy and security.

Navigating Data Privacy: Bangladesh’s Emerging Framework
The concept of data privacy and the accompanying data protection rights and requirements are relatively new in Bangladesh. However, in this era of rapid digital development, social networking, cybercrime, artificial intelligence, electronic communication, and increasing user awareness, they have never been more crucial. Data protection encompasses a set of privacy laws, policies, and procedures aimed at minimizing intrusion into individuals’ privacy caused by the collection, storage, and dissemination of personal data.
Key Legal Frameworks
The Constitution: Article 43 of the Constitution grants every citizen the right to privacy in correspondence and other means of communication. Additionally, other fundamental rights such as freedom of thought, speech, and personal liberty also incorporate aspects of privacy.
Information Communication Technology Act 2006: This act recognizes electronic transactions and imposes responsibilities on entities handling sensitive personal data. It mandates the implementation of reasonable security practices to prevent wrongful loss or gain.
Digital Security Act 2018: Enacted to ensure national data security, this law addresses data crime identification, prevention, suppression, and trial. It grants authorities powers to intervene in digital media activities threatening data security.
Telecommunication Act 2001: Regulates electronic communication and grants powers to intercept data for reasons of national security and public order. It also imposes penalties for unauthorized interception of communication.
Consumer Rights Protection Act 2009: Provides penalties for acts detrimental to service receivers’ lives or security, imposing responsibilities on service providers to protect consumer data.
Penal Code 1860: Offers remedies against data theft through offenses such as misappropriation, theft, and criminal breach of trust.
Copyright Act 2000: Protects intellectual property rights, including computer databases, against unauthorized copying and distribution.
Emerging Data Protection Bill: A forthcoming legislation aiming to introduce concepts like data localization and adopt, principles from the General Data Protection Regulation (GDPR).
Public Sector: Although there is no specific law, the Digital Security Act addresses offenses committed through digital means under the Official Secrets Act 1923.
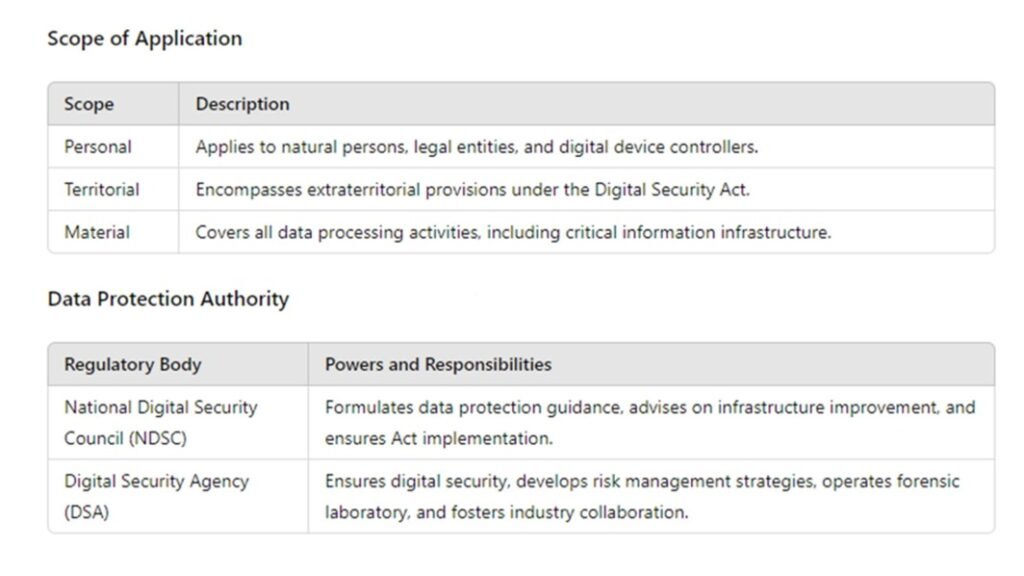
Scope of Application
Personal Scope:
Data protection laws apply to any natural person or legal entity, including institutions, companies, partnerships, farms, or other organizations. This encompasses digital device controllers and entities created by law.
Territorial Scope:
The following extraterritorial provisions are stipulated under the Digital Security Act:
- Offenses committed outside Bangladesh, punishable under these provisions, are treated as if they occurred within Bangladesh.
- Offenses committed in Bangladesh from outside using Bangladesh-based digital resources are subject to Bangladeshi law.
- Offenses committed outside Bangladesh by individuals within Bangladesh fall under Bangladeshi jurisdiction.
Material Scope:
The Digital Security Act covers all data processing activities, including usage, storage, and transmission, relating to various data types, including critical information infrastructure. It explicitly includes certain personal data under ‘identity information’.
Data Protection Authority
Main Regulator:
Under the Digital Security Act, the National Digital Security Council (NDSC) formulates and issues data protection guidance. However, for executive matters like content blocking or data decryption, the Digital Security Agency (DSA) holds executive power.
Powers and Responsibilities
National Digital Security Council (NDSC)
- Issuing directions to address digital security threats.
- Advising on infrastructure improvement and manpower enhancement.
- Enacting inter-institutional policies for digital security.
- Ensuring implementation of the Digital Security Act and related rules.
Digital Security Agency (DSA)
- Ensuring digital security of critical infrastructure.
- Developing risk management strategies.
- Establishing digital security standards and procedures.
- Operating Digital Forensic Laboratory.
- Addressing digital device crimes and cybercrimes.
- Facilitating digital security research and collaboration.
- Inspecting and monitoring digital security implementation.
- Participating in national security-related digital security issues.
- Fostering digital security-related industries.
- Collecting and analyzing global digital security information.
- Investigating digital security weaknesses and breaches.
In conclusion, digital interactions continue to permeate daily life, and ensuring robust data protection mechanisms becomes imperative to safeguard individuals’ rights and foster trust in the digital ecosystem.


